Exciting Opportunity: AWS Summit in Washington, DC – A Must-Attend Event for Public Sector
Are you ready to dive into the future of cloud technology and its impact on the public sector? Mark your calendars for June 26-27, 2024, as the AWS Summit Washington, DC takes center stage at the Walter E. Washington Convention Center. This free event offers public sector professionals a chance to explore the latest in cloud innovation, network with industry leaders, and gain invaluable insights into digital transformation. This year there is a focus on Gen AI.
Tech Reformers at AWS Summit
We’re thrilled to announce that Tech Reformers, an AWS Partner specializing in Public Sector solutions and with a particular focus on Education, will attend this timely event. Our team looks forward to engaging with attendees and sharing our expertise in leveraging AWS to drive innovation in government and educational institutions.
Event Highlights
Immerse yourself in the latest AWS innovation with over 300 sessions covering a wide range of topics. You’ll learn directly from AWS experts about accelerating your mission through technology. The event provides unparalleled networking opportunities (other than AWS re:Invent which we will be attending in December), allowing you to connect with public sector industry leaders, AWS professionals, and innovative partners like Tech Reformers.
Hands-on Learning and Customization
Enhance your skills through interactive workshops, whiteboard case studies, and solution-building sessions. The AWS Summit caters to professionals at all levels. Whether you’re a decision-maker, technical leader, or developer, you can tailor your agenda to suit your specific interests and needs.
Keynote Address
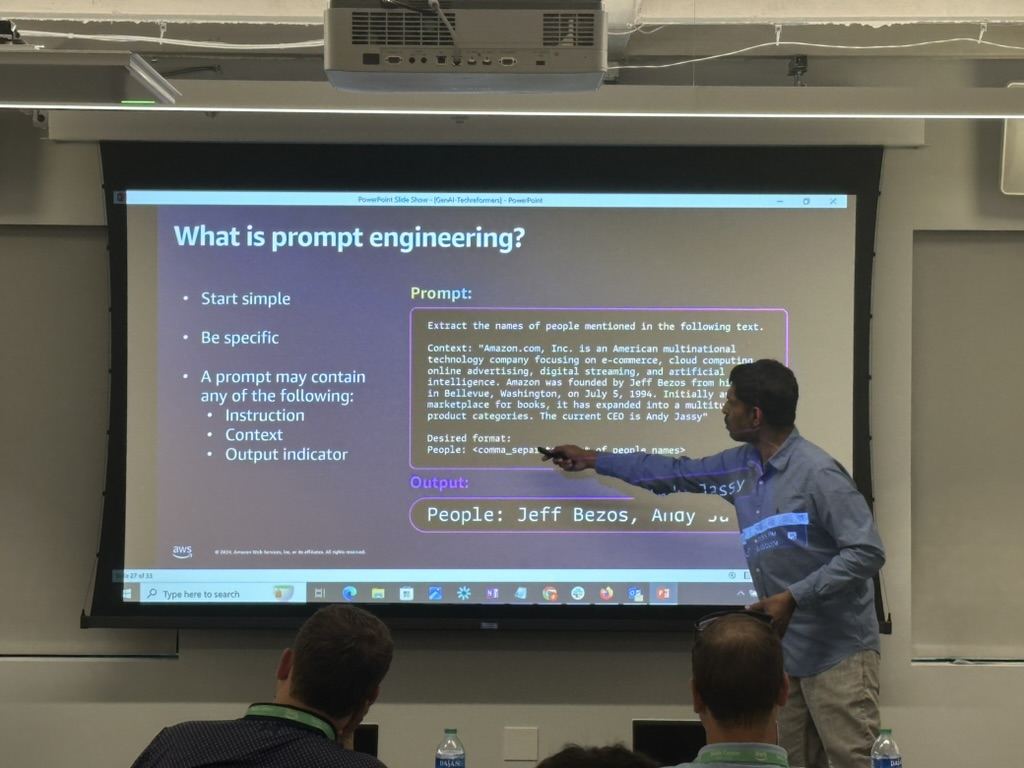
Don’t miss the keynote speech by Dave Levy, VP of AWS Worldwide Public Sector. His address will focus on the generative AI revolution and its impact on public sector services. You’ll gain insights into how AWS empowers organizations to be at the forefront of technological advancements while maintaining security and efficiency.
Free to Attend & Learn
Unlike re:Invent, his event is completely free to attend, making it an accessible opportunity for professionals across the public sector. Take advantage of this chance to learn, innovate, and connect without any financial barriers.
Connect with Tech Reformers
As an AWS Partner with deep expertise in the Public Sector, particularly in Education, Tech Reformers offers unique insights into cloud-based solutions for government and educational institutions. We understand the specific challenges and opportunities in these sectors and can help you navigate the complexities of digital transformation.
So, why connect with us at the event? We can discuss how to:
- Optimize your AWS infrastructure for public sector needs with our AWS QuickStart.
- Implement secure and compliant cloud solutions
- Leverage AI and machine learning in education and government services
- Streamline operations and reduce costs through cloud adoption
Finally, don’t miss this chance to learn, connect, and innovate. Join us at the AWS Summit Washington, DC and be part of shaping the future of public sector technology. And, reach out to Tech Reformers today to schedule a meeting at the event and explore how we can help transform your organization’s cloud strategy.